Internal Portal
Internal Portal Keycloak
Internal portal user management using Keycloak identity management solutions more detailed installation and user manuals can be found from https://www.keycloak.org/
Create database for internal portal Keycloak. Example „dmss_intportal_keycloak".
- Run docker container
In docker execution command Update:
a. database connection values accroring to database setup and credentials:
DB_ADDR= 192.168.2.215
DB_PORT= 5432
DB_DATABASE= dmss_intportal_keycloak
DB_USER= dmss_intportal_keycloak
DB_PASSWORD= dmss_intportal_keycloak
b. Server name and port:
HOST_NAME=http://dmee-keit-new.trustlynx.local:9998
KEYCLOAK_FRONTEND_URL=http://dmee-keit-new.trustlynx.local:9998/auth
docker run --network signbox --name=int-portal-keycloak --restart always -p 83:8080 -p 85:8088 -e HOST_NAME=http://dmee-keit-new.trustlynx.local:9998 -e keycloak_auth_url=http://dmee-keit-new.trustlynx.local:9998 -e KEYCLOAK_FRONTEND_URL=http://dmee-keit-new.trustlynx.local:9998/auth -e PROXY_ADDRESS_FORWARDING=true -e KEYCLOAK_USER=admin -e KEYCLOAK_PASSWORD=admin -e DB_VENDOR=postgres -e DB_ADDR=192.168.2.215 -e DB_PORT=5432 -e DB_DATABASE=dmss_intportal_keycloak -e DB_USER=dmss_intportal_keycloak -e DB_PASSWORD=dmss_intportal_keycloak jboss/keycloak:16.1.1
- Keycloak setup
a. Open browser URL (replace server name accordingly): http://dmee-keit-new.trustlynx.local:83/auth/admin/
b. Login as user „admin" and password „admin"
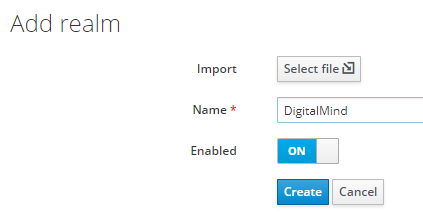
c. Create new realm „DigitalMind"
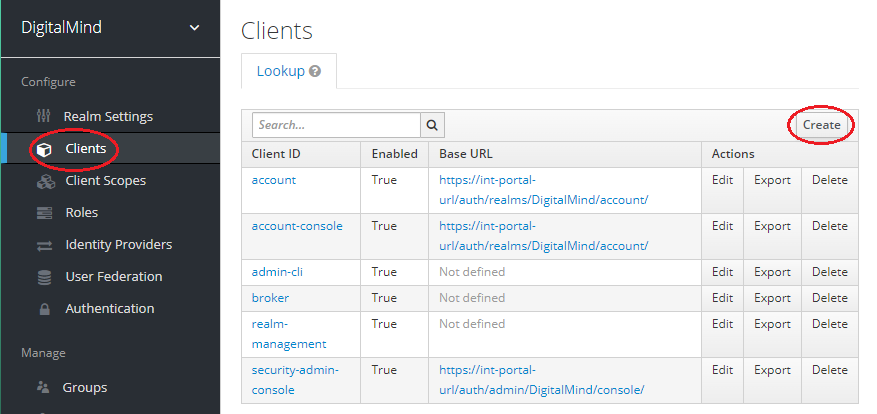
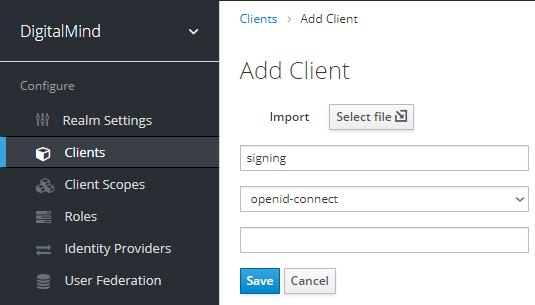
d. Create new client „signing"
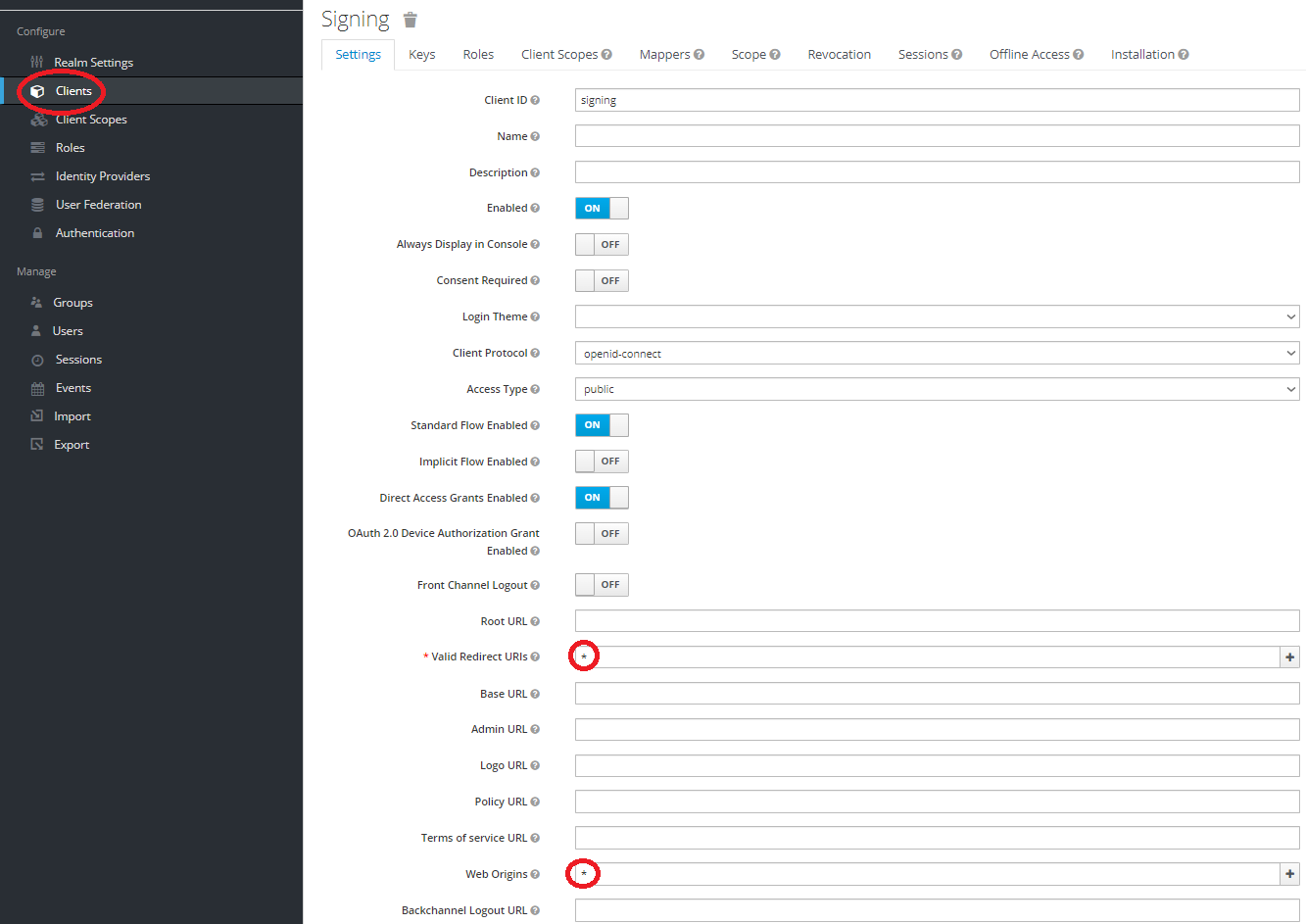
e. Set client valid redirect and web origins „*"
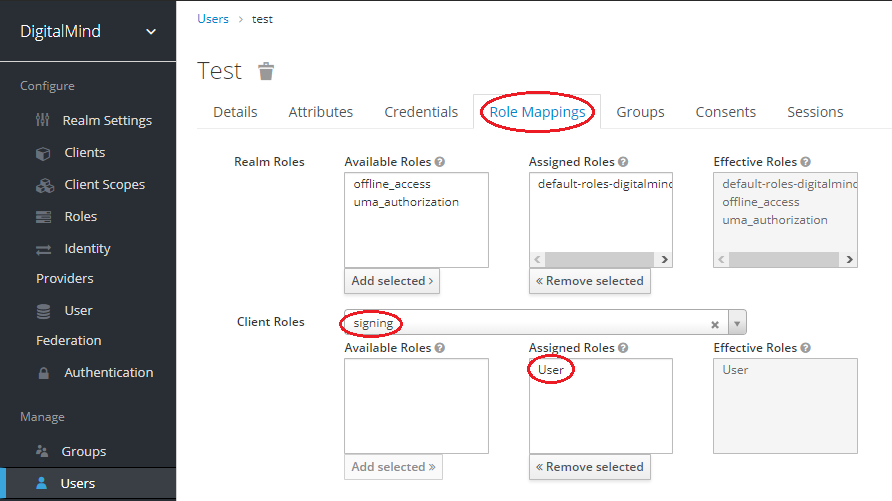
f. Create new role „User"
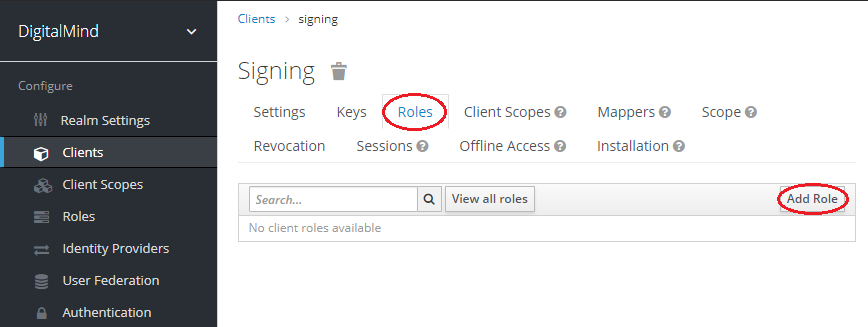
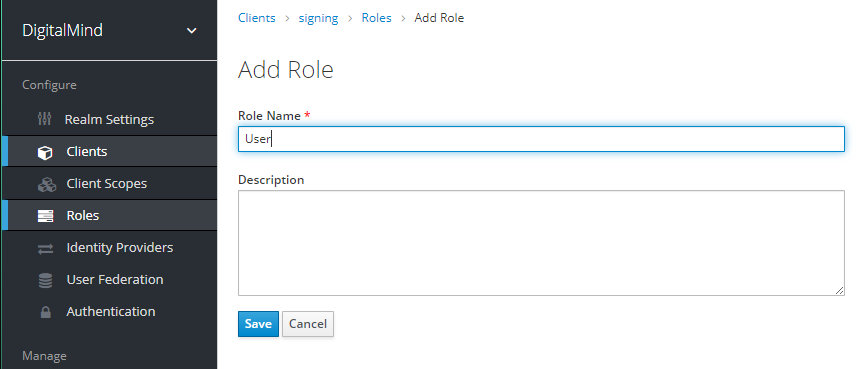
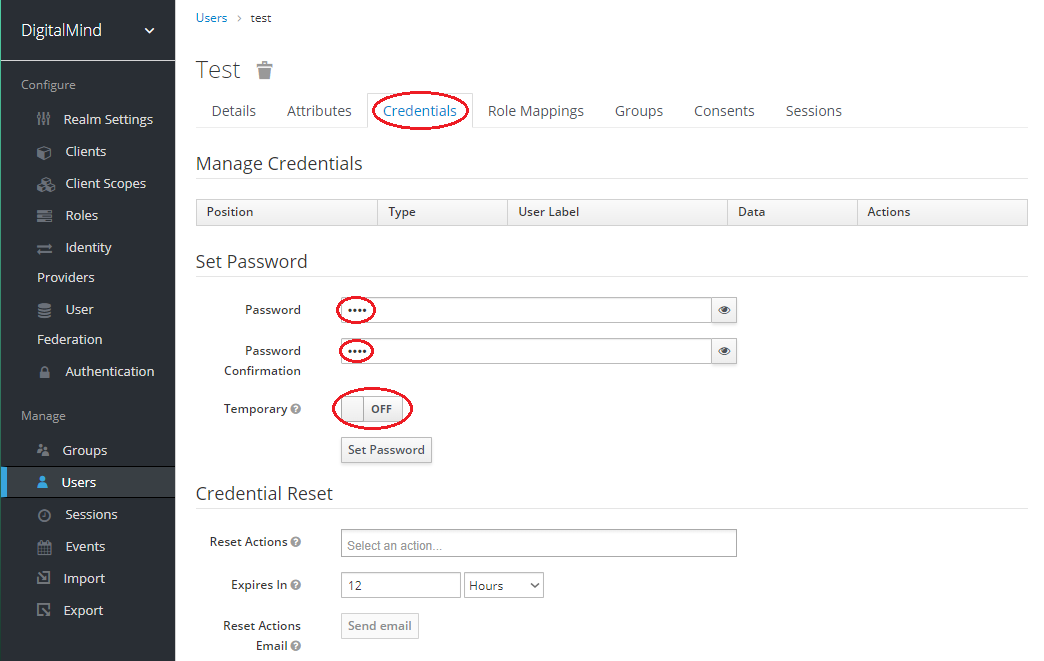
g. Create new user „test" and assign client role „User"
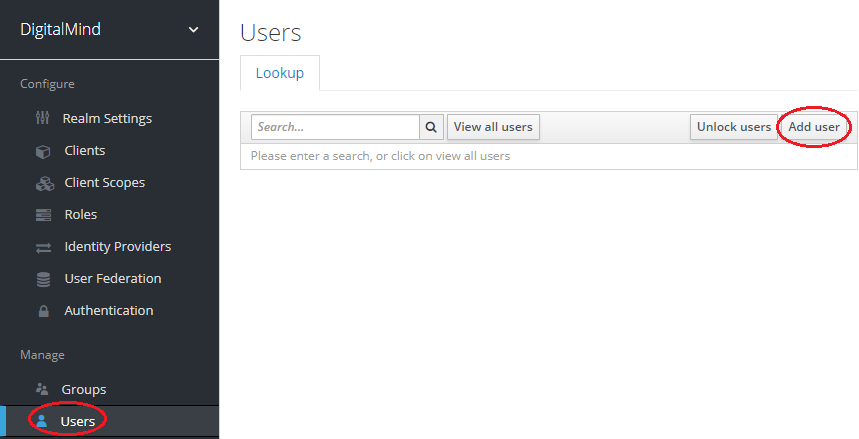
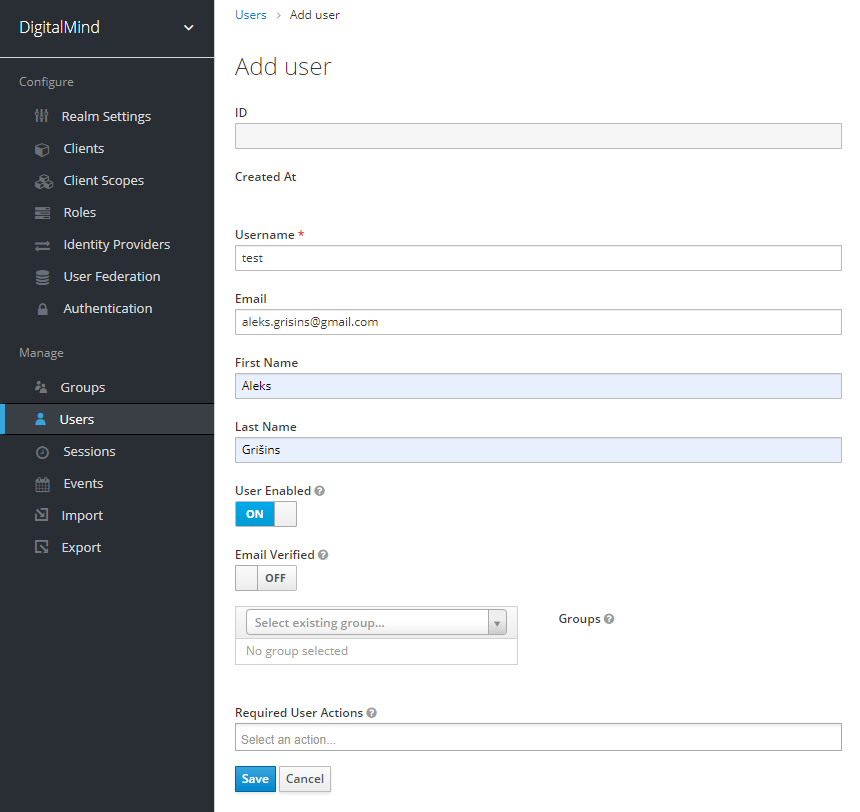
Internal Portal Gateway (int-portal-gateway)
Configuration updates
a. Update routed services URL according to service addresses
proxy:
servers:
Container and signature services
matchers: /api/container, /api/signing, /api/pdf, /api/stamping
server: http://dmss-container-and-signature-services:8092
Archive services
matchers: /api/document, /api/v2/document, /api/v2/auth
server: http://dmss-archive-services:8090
Process and audit services
matchers: /api/process, /api/auditing
server: http://dmss-process-and-auditing-service:8765
- Users and groups mappings and roles. Under groupconfigurations defined list of groups enabled to use "Internal Portal". User groups tested against user assigned "Roles" in Keycloak "signing" client. User group mapping includes scope parameter with one of following values:
"USER" – members of specified group see and manage only his/her initiated process in processes list
"GROUP" – members of specified group see and manage all current group members-initiated processes in processes list
"ADMIN" – members of specified group see and manage all initiated processes of any in processes list
Example of group mapping
usersandgroups:
groupconfigurations:
groupName: User
scope: USER
jwt: asd
Run docker container
docker run --network signbox --name=int-portal-gateway --restart always -p 89:8181 -v C:/docker/int-portal-gateway/:/confs -e SPRING_CONFIG_LOCATION=/confs/ digitalmindss/proxy:1.0.12.3
Internal Portal Static (int-portal-static)
-
Configuration updates
-
Update server name in config.js file accordingly
window.SIGNING\_PATH = "http://dmee-keit-new.trustlynx.local:9998/intproxy/api/";window.KEYCLOAK_CONFIG = { -
Run docker container
docker run --network signbox --name=int-portal-static --restart always -p 90:80 -v C:/docker/int-portal-static/locales/:/usr/share/nginx/html/public/assets/locales/ -v C:/docker/int-portal-static/nginx.conf:/etc/nginx/conf.d/default.conf -v C:/docker/int-portal-static/:/usr/share/nginx/html/config/ digitalmindss/int-portal-static:1.7.1.1